In yesterday's diary, I discussed a new proposed top-level domain, ".internal". This reminded me to talk a bit about what a top-level domain is all about, and some different ways to look at the definition of a top-level domain.
Tag Archives: SANS
Infocon: green
The Fun and Dangers of Top Level Domains (TLDs), (Wed, Jan 31st)
In the beginning, life was easy. We had a very limited set of top-level domains: .com, .edu, .gov, ..int, org, .mil, .net, .org, .edu. In addition, we had .arpa for infrastructure use and various two letter country level domains.
But that initial set of TLDs was insufficient as the internet grew, and we had several additions:
- International Domains (IDN) allow for Punycode-encoded Unicode characters.
- Generic top-level domains, allowing anybody to apply for a TLD of their choice.
- A few special use TLDs like .example, .invalid, .local, .onion and .test
And I am only considering ICANN-sanctioned TLDs. We also have a couple of alternate roots.
ICANN is consistently expanding the gTLDs. But yesterday, I noticed some news about a new interesting TLD that you may want to consider adopting: .internal.
Until now, there has been no "official" TLD for internal use. ".local" is reserved for multicast DNS, and using it internally can lead to odd conflicts if your unicast and multicast DNS processes overlap. Companies have run into issues with "adopting" unused top-level domains if they become official and used. For example, the European router manufacturer AVM used "fritz.box" for the internal admin interface of its popular "FRITZ!Box" line of routers.
First, many of these issues disappear if you use a properly registered domain name. You may, for example, register "example-internal.com" for internal use. For external users, you can configure a wildcard entry directing users to a static placeholder page. It will also be easy to get proper TLS certificates for hosts within the domain, should you need them.
But if you do not want to register a "proper" domain for internal use, or if you feel like you need a TLD, you can now use ".internal" without being afraid that the TLD will be used publicly elsewhere.
What are the risks of using ".internal"?
Other networks may use it, too. If you later need to merge your network with another organization, let's say, a partner, or as part of a merge, you may have overlapping names. This issue is similar to the one you will have when using RFC1918 IP addresses.
The biggest security threat comes from users who are only connected to your network part of the time. They may attempt to resolve the internal hostnames while connected to external networks. In a non-malicious network, they may accidentally connect to ".internal" hosts defined at the external network. For a malicious network, there is no big difference. An attacker may intercept DNS requests no matter if they are directed at .internal or another TLD. However, an official domain may make it easier to configure proper TLS certificates. ".internal" TLS certificates will only work with an internal certificate authority. TLS remains one of the main defenses against DNS spoofing, particularly if you use a malicious resolver.

—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
What did I say to make you stop talking to me?, (Tue, Jan 30th)
We use Cowrie to emulate an SSH and Telnet server for our honeypots. Cowrie is great software maintained by Michel Oosterhof [1]. The honeypot is a reasonable emulation of such a server, easy to maintain, and very feature-rich for even more advanced analysis. We only use it in its simplest form for our DShield sensor.
Exploit Flare Up Against Older Altassian Confluence Vulnerability, (Mon, Jan 29th)
Last October, Atlassian released a patch for %%cve:2023-22515%% [1]. This vulnerability allowed attackers to create new admin users in Confluence. Today, I noticed a bit a "flare up" in a specific exploit variant.
Rapid 7 published a good summary of the vulnerability [2]. As so often, the vulnerability is pretty straightforward once you see it. During the initial setup, Confluence asks the user to configure an administrator. After setup is complete, the user needs to log in using this initial administrator account to configure additional users. Using the vulnerability, an attacker can flip the "setup complete" state. No authentication is required to do so. An attacker can first enable the initial setup behavior, us it to add a new administrator account, and complete the attack by disabling the setup page to make the application appear normal for other users.
In it's blog, Rapid 7 suggests the following URL to trigger the exploit, and switch Confluence into "Setup" mode:
curl -vk http://192.168.86.50:8090/server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=false
The exploit we are seeing is a bit different:
GET /server-info.action?bootstrapStatusProvider.applicationConfig.setupComplete=0&cache2baSyYzftjSFREWn8TtL8AKl6pM HTTP/1.1
Host: [victim IP]:8090
User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/34.0.1866.237 Safari/537.36
Connection: close
Accept-Encoding: gzip
Aside from using "0" instead of "False" (which is equivalent), the attacker also adds the "cache…" string at the end. This may be to avoid retrieving cached responses and to ensure the attack string will reach the vulnerable server. Without this string, the attacker may just receive the response from an earlier attack attempt and not the actual server response. The "cache" string is constant and not randomized between requests, which caused this attack to show up in our "First Seen" list again.
This attack version originates mostly from %%ip:206.188.196.230%%, The server hosted in the is likely compromised. It has been scanning since yesterday, and it is also hosting a known phishing website.
—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
A Batch File With Multiple Payloads, (Fri, Jan 26th)
Windows batch files (.bat) are often seen by people as very simple but they can be pretty complex or.. contain interesting encoded payloads! I found one that contains multiple payloads decoded and used by a Powershell process. The magic is behind how comments can be added to such files. The default (or very common way) is to use the "REM" keyword. But you can also use a double-colon:
Facebook AdsManager Targeted by a Python Infostealer, (Thu, Jan 25th)
How Bad User Interfaces Make Security Tools Harmful, (Wed, Jan 24th)
User interface design is one of those often overlooked aspects in software design in general. A bad user interface can quickly become a vulnerability regarding security. Even though I do not remember actual CVE's assigned to bad user-interface design, there probably should be some. One of the more famous user interface design issues was the "Therac-25" radiation treatment device. A bad user interface has been blamed for contributing to some deadly accidents [1].
The issue I am considering here is that it is unlikely to kill someone. Still, they need to make it easier for regular users and security professionals to identify problems accurately and adequately respond to security incidents. I am not naming/shaming any specific products here. The examples shown are representative for pretty much any current consumer security tool.
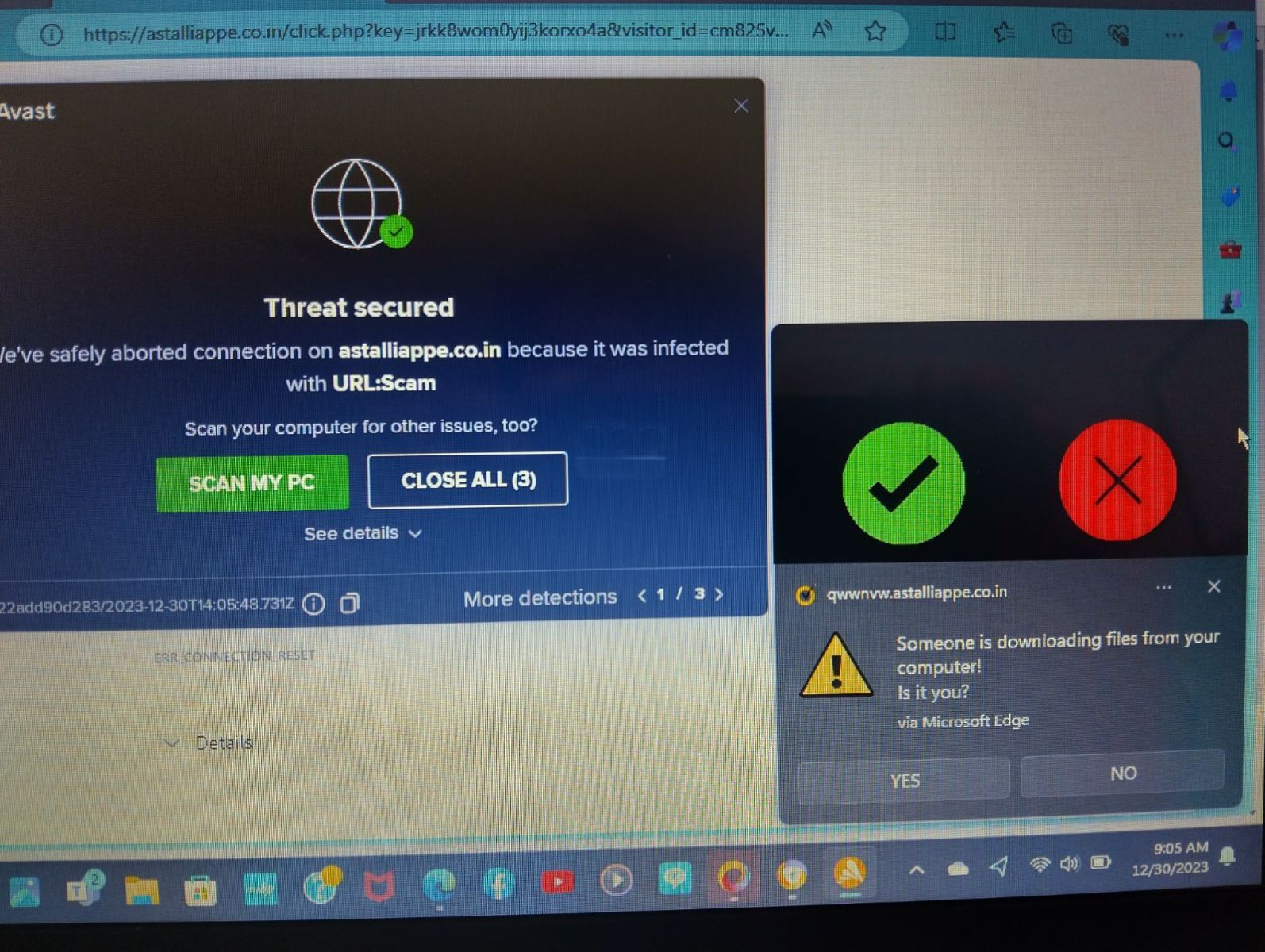
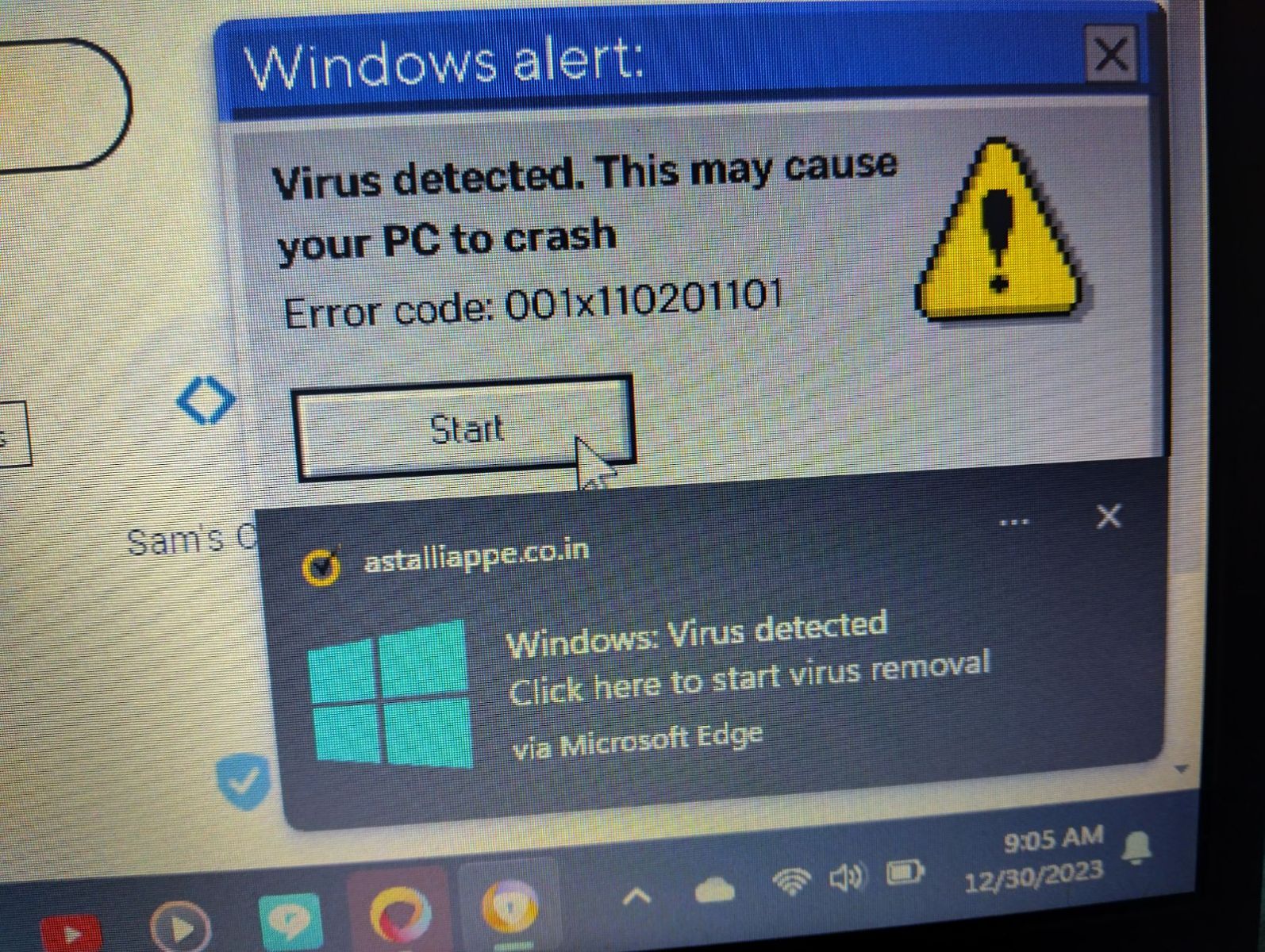
Like many of our readers, I often receive requests for help from family, friends, and neighbors. Here is a typical screenshot I received from one:
For this post, it is good to have these "mobile phone screenshots." It shows what messages the user considers important. How long did it take you to find the real anti-malware message among the fake ones? The user clicked on the wrong one, leading to a fake tech support line. Luckily, the fake tech support company asked for more money than the user could pay. However, the victim still had additional malware installed on the system.
Security companies, in particular in the consumer space, often use popup notifications as a sales tool to convince users of the value of the product. I remember the early versions of the Windows firewall "Zone Alarm". For each rejected packet, it showed a popup notification. Of course, this quickly became too annoying as bots started to proliferate.
This isn't just an issue with one particular product. All are the same. The popup is also often not useful enough for a more skilled server to understand what is happening. For example this popup from a different product:
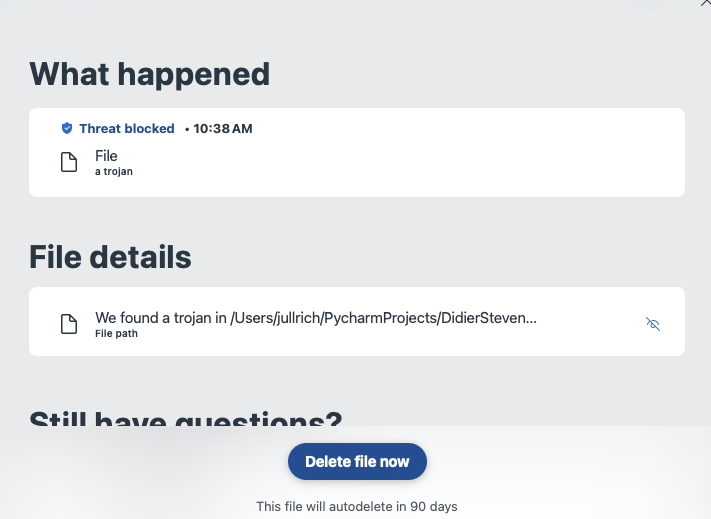
The popup above is from an Anti-Malware product I am running on my system. The filename is cut off, and I have not found a way to get the full path/filename. Instead, I am left guessing if this is a false positive or real malware. In this particular case, some of you may recognize the name in the path, and this gave it away to me why the alert popped up. But in particular, in cases where the malware arrived as an email attachment, it will be in a "random named" folder, and little is displayed about what the malware is about and what it would do if executed.
As a consumer, we need fewer alerts. I do not need to know that a particular attachment is malicious unless I try to execute it. Same for websites. You can just block access to the site. By the time the fake popups show up, your product failed. Security companies need to invest more in better user interface research to communicate threats to users of various skill levels accurately and effectively.
Most requests for help I get from non-technical users are for false positives and fake attacks, not actual infections. And for the remaining real infections, they are often caused by these users falling for a fake alert and trying to do the "right thing".
[1] https://en.wikipedia.org/wiki/Therac-25
—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Update on Atlassian Exploit Activity , (Tue, Jan 23rd)
Exploit activity against Atlassian Confluence servers has exploded since we first discussed it yesterday. The combination of a simple-to-exploit vulnerability and a potential set of high-value targets makes this an ideal vulnerability for many attackers.
Apple Updates Everything – New 0 Day in WebKit, (Mon, Jan 22nd)
Today, Apple released significant "point releases" for all its operating systems. With new features, we also got patches for 29 different vulnerabilities. The table below shows how some vulnerabilities affect multiple operating systems across the Apple ecosystem.
Three of the vulnerabilities are known to be already exploited, one of which is new, according to Apple:
CVE-2024-23222: This WebKit type-confusion vulnerability has already been exploited and is being patched in macOS as well as iOS.
CVE-2023-42916 and CVE-2023-42917 have been exploited against iOS versions before 16.7.1. These vulnerabilities are not new and were patched in newer versions of iOS and macOS in the past. They are not being patched for iOS/iPadOS 15.8
| iOS 17.3 and iPadOS 17.3 | iOS 16.7.5 and iPadOS 16.7.5 | iOS 15.8.1 and iPadOS 15.8.1 | macOS Sonoma 14.3 | macOS Ventura 13.6.4 | macOS Monterey 12.7.3 | watchOS 10.3 | tvOS 17.3 |
|---|---|---|---|---|---|---|---|
| CVE-2024-23212 [important] Apple Neural Engine The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | x | x | x | |
| CVE-2024-23218 [moderate] CoreCrypto A timing side-channel issue was addressed with improvements to constant-time computation in cryptographic functions. An attacker may be able to decrypt legacy RSA PKCS#1 v1.5 ciphertexts without having the private key |
|||||||
| x | x | x | x | ||||
| CVE-2024-23208 [important] Kernel The issue was addressed with improved memory handling. An app may be able to execute arbitrary code with kernel privileges |
|||||||
| x | x | x | x | ||||
| CVE-2024-23207 [moderate] Mail Search This issue was addressed with improved redaction of sensitive information. An app may be able to access sensitive user data |
|||||||
| x | x | x | x | x | |||
| CVE-2024-23223 [moderate] NSSpellChecker A privacy issue was addressed with improved handling of files. An app may be able to access sensitive user data |
|||||||
| x | x | x | x | ||||
| CVE-2024-23219 [moderate] Reset Services The issue was addressed with improved authentication. Stolen Device Protection may be unexpectedly disabled |
|||||||
| x | |||||||
| CVE-2024-23211 [moderate] Safari A privacy issue was addressed with improved handling of user preferences. A user's private browsing activity may be visible in Settings |
|||||||
| x | x | x | x | ||||
| CVE-2024-23203 [moderate] Shortcuts The issue was addressed with additional permissions checks. A shortcut may be able to use sensitive data with certain actions without prompting the user |
|||||||
| x | x | ||||||
| CVE-2024-23204 [moderate] Shortcuts The issue was addressed with additional permissions checks. A shortcut may be able to use sensitive data with certain actions without prompting the user |
|||||||
| x | x | x | |||||
| CVE-2024-23217 [moderate] Shortcuts A privacy issue was addressed with improved handling of temporary files. An app may be able to bypass certain Privacy preferences |
|||||||
| x | x | x | |||||
| CVE-2024-23215 [important] TCC An issue was addressed with improved handling of temporary files. An app may be able to access user-sensitive data |
|||||||
| x | x | x | x | ||||
| CVE-2024-23210 [moderate] Time Zone This issue was addressed with improved redaction of sensitive information. An app may be able to view a user's phone number in system logs |
|||||||
| x | x | x | x | ||||
| CVE-2024-23206 [moderate] WebKit An access issue was addressed with improved access restrictions. A maliciously crafted webpage may be able to fingerprint the user |
|||||||
| x | x | x | x | x | |||
| CVE-2024-23213 [critical] WebKit The issue was addressed with improved memory handling. Processing web content may lead to arbitrary code execution |
|||||||
| x | x | x | x | x | |||
| CVE-2024-23214 [critical] WebKit Multiple memory corruption issues were addressed with improved memory handling. Processing maliciously crafted web content may lead to arbitrary code execution |
|||||||
| x | x | x | |||||
| CVE-2024-23222 [critical] WebKit A type confusion issue was addressed with improved checks. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been exploited. |
|||||||
| x | x | x | x | x | x | ||
| CVE-2023-42937 [moderate] Accessibility A privacy issue was addressed with improved private data redaction for log entries. An app may be able to access sensitive user data |
|||||||
| x | x | x | |||||
| CVE-2023-38545 [moderate] curl Multiple issues were addressed by updating to curl version 8.4.0. Multiple issues in curl |
|||||||
| x | x | x | |||||
| CVE-2023-38039 [moderate] curl Multiple issues were addressed by updating to curl version 8.4.0. Multiple issues in curl |
|||||||
| x | x | x | |||||
| CVE-2023-38546 [moderate] curl Multiple issues were addressed by updating to curl version 8.4.0. Multiple issues in curl |
|||||||
| x | x | x | |||||
| CVE-2023-42915 [moderate] curl Multiple issues were addressed by updating to curl version 8.4.0. Multiple issues in curl |
|||||||
| x | x | x | |||||
| CVE-2023-42888 [important] ImageIO The issue was addressed with improved checks. Processing a maliciously crafted image may result in disclosure of process memory |
|||||||
| x | x | x | |||||
| CVE-2023-42916 [moderate] WebKit An out-of-bounds read was addressed with improved input validation. Processing web content may disclose sensitive information. Apple is aware of a report that this issue may have been exploited against versions of iOS before iOS 16.7.1. |
|||||||
| x | |||||||
| CVE-2023-42917 [critical] WebKit A memory corruption vulnerability was addressed with improved locking. Processing web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been exploited against versions of iOS before iOS 16.7.1. |
|||||||
| x | |||||||
| CVE-2024-23224 [moderate] Finder The issue was addressed with improved checks. An app may be able to access sensitive user data |
|||||||
| x | x | ||||||
| CVE-2024-23209 [critical] LLVM The issue was addressed with improved memory handling. Processing web content may lead to arbitrary code execution |
|||||||
| x | |||||||
| CVE-2023-40528 [important] Core Data This issue was addressed by removing the vulnerable code. An app may be able to bypass Privacy preferences |
|||||||
| x | |||||||
| CVE-2023-42935 [moderate] LoginWindow An authentication issue was addressed with improved state management. A local attacker may be able to view the previous logged in user?s desktop from the fast user switching screen |
|||||||
| x | |||||||
| CVE-2023-42887 [moderate] NSOpenPanel An access issue was addressed with additional sandbox restrictions. An app may be able to read arbitrary files |
|||||||
| x | |||||||
—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.