We are excited to announce that the August update to the PowerShell Extension for Visual Studio Code is now available on the extension marketplace.
This release adds a walkthrough experience for getting started with PowerShell in VS Code, more regression tests, a major LSP client library update, and includes a number of bug fixes!
Updates in the August Release
Note that these updates all shipped in our PowerShell Preview Extension for VS Code before shipping in our stable channel.
Some highlights of August releases:

 vscode-powershell #4151 Add
vscode-powershell #4151 Add integratedConsole.startInBackgroundto completely hide the terminal.
 vscode-powershell #4080 Create a walkthrough experience for PowerShell. (Thanks @S-Hakim!)
vscode-powershell #4080 Create a walkthrough experience for PowerShell. (Thanks @S-Hakim!)- #⃣

 vscode-powershell #4141 Improve language client library close action message.
vscode-powershell #4141 Improve language client library close action message. 
 PowerShellEditorServices #1892 Add symbols for Pester setup and teardown blocks. (Thanks @fflaten!)
PowerShellEditorServices #1892 Add symbols for Pester setup and teardown blocks. (Thanks @fflaten!)
 PowerShellEditorServices #1891 Fix whitespace in Pester symbol and add test. (Thanks @fflaten!)
PowerShellEditorServices #1891 Fix whitespace in Pester symbol and add test. (Thanks @fflaten!)
 PowerShellEditorServices #1887 Fix symbol highlight when hovering function name. (Thanks @fflaten!)
PowerShellEditorServices #1887 Fix symbol highlight when hovering function name. (Thanks @fflaten!)
 PowerShellEditorServices #1897 – Add artificial stack frame to represent contexts without one.
PowerShellEditorServices #1897 – Add artificial stack frame to represent contexts without one.
 PowerShellEditorServices #1894 – Fix stepping while watch expressions or interactive pipeline is running.
PowerShellEditorServices #1894 – Fix stepping while watch expressions or interactive pipeline is running.
 vscode-powershell #4128 – Update
vscode-powershell #4128 – Update vscode-languageclientand refactor (a lot of TLC).
 vscode-powershell #3266 – Fix debugger to start language client when necessary.
vscode-powershell #3266 – Fix debugger to start language client when necessary.
 vscode-powershell #4120 Remove extraneous
vscode-powershell #4120 Remove extraneous )from the do-while snippet. (Thanks @ncook-hxgn!)
 PowerShellEditorServices #1874 Add end-to-end integration test with Vim.
PowerShellEditorServices #1874 Add end-to-end integration test with Vim.
 vscode-powershell #4112 Fix (and test) regression with PSScriptAnalyzer default rules.
vscode-powershell #4112 Fix (and test) regression with PSScriptAnalyzer default rules.
 PowerShellEditorServices #1872 Add regression tests for parse error DiagnosticMarkers. (Thanks @fflaten!)
PowerShellEditorServices #1872 Add regression tests for parse error DiagnosticMarkers. (Thanks @fflaten!)
 PowerShellEditorServices #1869 – Fix duplicate DiagnosticMarkers when reopening a file. (Thanks @fflaten!)
PowerShellEditorServices #1869 – Fix duplicate DiagnosticMarkers when reopening a file. (Thanks @fflaten!)
 vscode-powershell #4100 Remove popup when extension updates.
vscode-powershell #4100 Remove popup when extension updates.
 PowerShellEditorServices #1867 – Add regression test for when
PowerShellEditorServices #1867 – Add regression test for when promptis undefined.
 vscode-powershell #4073 – Fix bug where error in
vscode-powershell #4073 – Fix bug where error in promptfunction crashed REPL.
For the full list of changes please refer to our changelog.
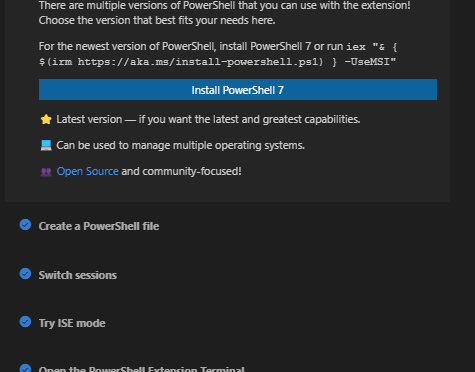
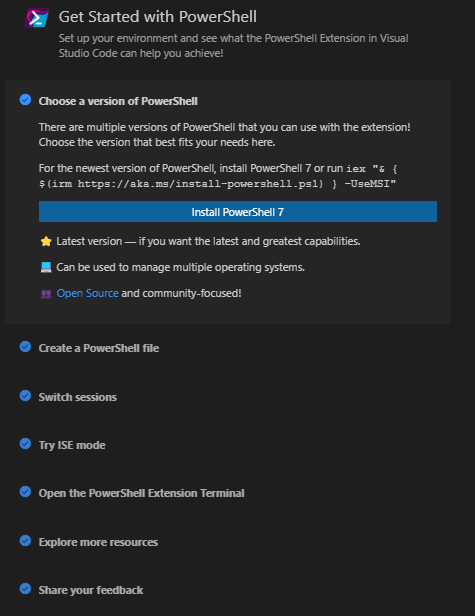
Getting Started Walkthrough
As a part of this release we have introduced a getting started experience for PowerShell in VS Code. This experience was designed through a series of customer surveys and interviews conducted by our summer intern. The walkthrough can be accessed on the Getting Started page in VS Code, or through the command pallette.
We look forward to getting more feedback on this walkthrough and learning how we can improve it.
LSP Client Library Update
This release also includes a major update to our LSP client library dependency, vscode-languageclient. The extension uses this library to start, connect, and communicate with the LSP server, PowerShell Editor Services.
By incorporating this update in vscode-powershell #4128 we were able to prevent a number of race conditions that could be encountered during startup, as the latest version of this library allows us to register our notification and request handlers before starting the server. The lifecycle management code was also given some much needed attention, and so startup and shut-down is now a more stable experience.
Please note that due to an upstream change, there is now a second notification when the server is stopped. We are working with the upstream team to de-duplicate this popup, and are also contemplating enabling a configurable auto-restart of the server.
Getting Support and Giving Feedback
While we hope the new implementation provides a much better user experience, there are bound to be issues. Please let us know if you run into anything.
If you encounter any issues with the PowerShell Extension in Visual Studio Code or have feature requests, the best place to get support is through our GitHub repository.
Sydney Smith and Andy Jordan PowerShell Team
The post PowerShell Extension for Visual Studio Code August 2022 Update appeared first on PowerShell Team.