The info is spreading across the news websites: For approximatively two hours, many online services or websites are suffering of an Amazon Web Services outage. Some affected services:
Tag Archives: SANS
Using Syscall() for Obfuscation/Fileless Activity, (Mon, Oct 20th)
I found another piece of malware this weekend. This one looks more like a proof-of-concept because the second-stage payload is really "simple", but it attracted my attention because it uses a nice technique to obfuscate the code.
The dropper is a simple Python script (SHA256:e6f7afb92153561ff6c584fee1b04fb132ba984e8a28ca63708a88ebad15b939) with a low VT score of 4/62[1]. The script contains an embedded Base64 payload that, once decoded, will be executed. This second stage is an ELF file, indicating the script targets a Linux system.
What attracted my attention is the direct use of syscall()[2] instead of classic functions:
import ctypes libc = ctypes.CDLL(None) syscall = libc.syscall [...] fd = syscall(319, "", 1) os.write(fd, content)
A full list of available syscalls is documented by many websites[3]. The syscall 319 is "memfd_create" and, as the name suggests, it allows creating a file descriptor in memory (read: without touching the filesystem).
The Base64 payload is not very interesting, it's an ELF file (SHA256:52fc723f7e0c4202c97ac5bc2add2d1d3daa5c3f84f3d459a6a005a3ae380119) that will just encrypt files using a 1-byte XOR key:
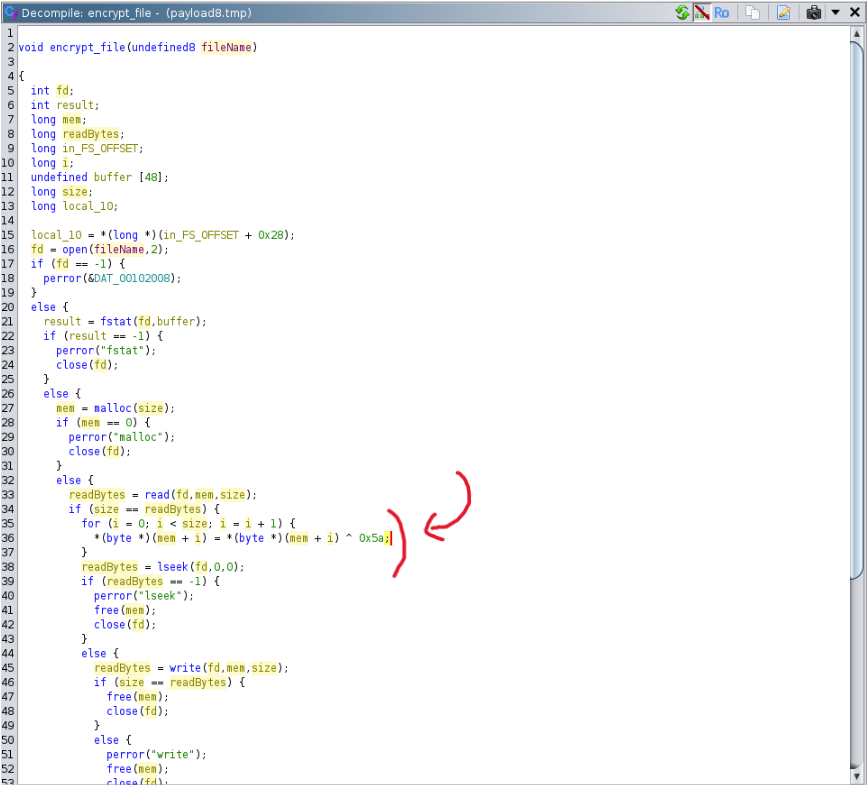
[1] https://www.virustotal.com/gui/file/e6f7afb92153561ff6c584fee1b04fb132ba984e8a28ca63708a88ebad15b939/detection
[2] https://man7.org/linux/man-pages/man2/syscalls.2.html
[3] https://www.chromium.org/chromium-os/developer-library/reference/linux-constants/syscalls/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler – Freelance Cyber Security Consultant
PGP Key
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
TikTok Videos Promoting Malware Installation, (Fri, Oct 17th)
New DShield Support Slack, (Thu, Oct 16th)
This week, we set up a new Slack workspace for DShield.org. This workspace replaces the old workspace we originally configured back in 2016 or 2017. The workspace was originally configured as a free workspace to support the DShield.org community. Over the years, it has had a good following and a good amount of traffic.
Clipboard Pictures Exfiltration in Python Infostealer, (Wed, Oct 15th)
For a while, clipboard content has been monitored by many infostealers. Purposes can be multiple, like simply searching and exfiltrating juicy data or on-the-fly modification like crypto-wallet swapping[1]. Note that the clipboard is a major risk when you don't disable clipboard sharing between your virtual machines and hosts. A malware running in a sandbox will access your (host) clipboard without problem!
Microsoft Patch Tuesday October 2025, (Tue, Oct 14th)
I am experimenting today with a little bit of a cleaned-up patch overview. I removed vulnerabilities that affect Microsoft's cloud systems (but appreciate Microsoft listing them at all), as well as vulnerabilities in third-party software like open source libraries. This should leave us with Microsoft-specific on-premises vulnerabilities. This month, this leaves 157 different vulnerabilities. Eight of the vulnerabilities are rated critical.
This month, Microsoft is discontinuing support for a number of different products:
- Windows 10
- Office 2016
- Exchange Server 2016
- Office 2019
- Exchange Server 2019
Office and Exchange users are directed towards cloud and subscription offerings. For Office, you still have Office 2024 available if you would rather "own" the product. For Exchange, the Exchange Server Subscription Edition is available as of July.
Windows 10 users will have the option to sign up for "Extended Security Updates" (ESU). It has been offered as a low-cost alternative to retain security updates, and in some countries, it is offered for free.
| Description | |||||||
|---|---|---|---|---|---|---|---|
| CVE | Disclosed | Exploited | Exploitability (old versions) | current version | Severity | CVSS Base (AVG) | CVSS Temporal (AVG) |
| .NET Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55247%% | No | No | – | – | Important | 7.3 | 6.4 |
| .NET, .NET Framework, and Visual Studio Information Disclosure Vulnerability | |||||||
| %%cve:2025-55248%% | No | No | – | – | Important | 4.8 | 4.2 |
| ASP.NET Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-55315%% | No | No | – | – | Important | 9.9 | 8.6 |
| Configuration Manager Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55320%% | No | No | – | – | Important | 6.7 | 5.8 |
| %%cve:2025-59213%% | No | No | – | – | Important | 8.4 | 7.3 |
| Copilot Spoofing Vulnerability | |||||||
| %%cve:2025-59272%% | No | No | – | – | Critical | 6.5 | 5.7 |
| %%cve:2025-59286%% | No | No | – | – | Critical | 6.5 | 5.7 |
| Data Sharing Service Spoofing Vulnerability | |||||||
| %%cve:2025-59200%% | No | No | – | – | Important | 7.7 | 6.7 |
| Desktop Windows Manager Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55681%% | No | No | – | – | Important | 7.0 | 6.1 |
| DirectX Graphics Kernel Denial of Service Vulnerability | |||||||
| %%cve:2025-55698%% | No | No | – | – | Important | 7.7 | 6.7 |
| DirectX Graphics Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55678%% | No | No | – | – | Important | 7.0 | 6.1 |
| Internet Information Services (IIS) Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59282%% | No | No | – | – | Important | 7.0 | 6.1 |
| JDBC Driver for SQL Server Spoofing Vulnerability | |||||||
| %%cve:2025-59250%% | No | No | – | – | Important | 8.1 | 7.1 |
| M365 Copilot Spoofing Vulnerability | |||||||
| %%cve:2025-59252%% | No | No | – | – | Critical | 6.5 | 5.7 |
| MITRE CVE-2025-54957: Integer overflow in Dolby Digital Plus audio decoder | |||||||
| %%cve:2025-54957%% | No | No | – | – | Important | 7.0 | 6.1 |
| MITRE: CVE-2025-59489 Unity Gaming Engine Editor vulnerability | |||||||
| %%cve:2025-59489%% | No | No | – | – | Important | 8.4 | 8.4 |
| Microsoft Brokering File System Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-48004%% | No | No | – | – | Important | 7.4 | 6.4 |
| %%cve:2025-59189%% | No | No | – | – | Important | 7.4 | 6.4 |
| Microsoft DWM Core Library Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-58722%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59254%% | No | No | – | – | Important | 7.8 | 6.8 |
| Microsoft Defender for Linux Denial of Service Vulnerability | |||||||
| %%cve:2025-59497%% | No | No | – | – | Important | 7.0 | 6.1 |
| Microsoft Excel Information Disclosure Vulnerability | |||||||
| %%cve:2025-59235%% | No | No | – | – | Important | 7.1 | 6.2 |
| %%cve:2025-59232%% | No | No | – | – | Important | 7.1 | 6.2 |
| Microsoft Excel Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59231%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59233%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59236%% | No | No | – | – | Critical | 8.4 | 7.3 |
| %%cve:2025-59243%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59223%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59224%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59225%% | No | No | – | – | Important | 7.8 | 6.8 |
| Microsoft Exchange Server Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-53782%% | No | No | – | – | Important | 8.4 | 7.3 |
| %%cve:2025-59249%% | No | No | – | – | Important | 8.8 | 7.7 |
| Microsoft Exchange Server Spoofing Vulnerability | |||||||
| %%cve:2025-59248%% | No | No | – | – | Important | 7.5 | 6.5 |
| Microsoft Failover Cluster Information Disclosure Vulnerability | |||||||
| %%cve:2025-47979%% | No | No | – | – | Important | 5.5 | 4.8 |
| %%cve:2025-59188%% | No | No | – | – | Important | 5.5 | 4.8 |
| Microsoft Failover Cluster Virtual Driver Information Disclosure Vulnerability | |||||||
| %%cve:2025-59260%% | No | No | – | – | Important | 5.5 | 4.8 |
| Microsoft Graphics Component Denial of Service Vulnerability | |||||||
| %%cve:2025-59195%% | No | No | – | – | Important | 7.0 | 6.1 |
| Microsoft Graphics Component Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-49708%% | No | No | – | – | Critical | 9.9 | 8.6 |
| Microsoft Office Denial of Service Vulnerability | |||||||
| %%cve:2025-59229%% | No | No | – | – | Important | 5.5 | 4.8 |
| Microsoft Office Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59234%% | No | No | – | – | Critical | 7.8 | 6.8 |
| %%cve:2025-59227%% | No | No | – | – | Critical | 7.8 | 6.8 |
| Microsoft Office Visio Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59226%% | No | No | – | – | Important | 7.8 | 6.8 |
| Microsoft PowerPoint Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59238%% | No | No | – | – | Important | 7.8 | 6.8 |
| Microsoft SharePoint Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59228%% | No | No | – | – | Important | 8.8 | 7.7 |
| %%cve:2025-59237%% | No | No | – | – | Important | 8.8 | 7.7 |
| Microsoft Windows File Explorer Spoofing Vulnerability | |||||||
| %%cve:2025-58739%% | No | No | – | – | Important | 6.5 | 5.7 |
| %%cve:2025-59214%% | No | No | – | – | Important | 6.5 | 5.7 |
| Microsoft Word Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59221%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-59222%% | No | No | – | – | Important | 7.8 | 6.8 |
| NTLM Hash Disclosure Spoofing Vulnerability | |||||||
| %%cve:2025-59185%% | No | No | – | – | Important | 6.5 | 5.7 |
| %%cve:2025-59244%% | No | No | – | – | Important | 6.5 | 5.7 |
| Network Connection Status Indicator (NCSI) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59201%% | No | No | – | – | Important | 7.8 | 6.8 |
| NtQueryInformation Token function (ntifs.h) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55696%% | No | No | – | – | Important | 7.8 | 6.8 |
| Playwright Spoofing Vulnerability | |||||||
| %%cve:2025-59288%% | No | No | – | – | Moderate | 5.3 | 4.9 |
| PowerShell Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-25004%% | No | No | – | – | Important | 7.3 | 6.4 |
| Remote Desktop Client Remote Code Execution Vulnerability | |||||||
| %%cve:2025-58718%% | No | No | – | – | Important | 8.8 | 7.7 |
| Remote Desktop Protocol Remote Code Execution Vulnerability | |||||||
| %%cve:2025-58737%% | No | No | – | – | Important | 7.0 | 6.1 |
| Remote Procedure Call Denial of Service Vulnerability | |||||||
| %%cve:2025-59502%% | No | No | – | – | Moderate | 7.5 | 6.5 |
| Software Protection Platform (SPP) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59199%% | No | No | – | – | Important | 7.8 | 6.8 |
| Storage Spaces Direct Information Disclosure Vulnerability | |||||||
| %%cve:2025-59184%% | No | No | – | – | Important | 5.5 | 4.8 |
| Storport.sys Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59192%% | No | No | – | – | Important | 7.8 | 6.8 |
| Virtual Secure Mode Spoofing Vulnerability | |||||||
| %%cve:2025-48813%% | No | No | – | – | Important | 6.3 | 5.5 |
| Visual Studio Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55240%% | No | No | – | – | Important | 7.3 | 6.4 |
| Windows Active Directory Federation Services (ADFS) Information Disclosure Vulnerability | |||||||
| %%cve:2025-59258%% | No | No | – | – | Important | 6.2 | 5.4 |
| Windows Agere Modem Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-24990%% | No | Yes | – | – | Important | 7.8 | 7.2 |
| %%cve:2025-24052%% | Yes | No | – | – | Important | 7.8 | 7.0 |
| Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59242%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-58714%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Authentication Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55701%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59277%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59275%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59278%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows BitLocker Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-55333%% | No | No | – | – | Important | 6.1 | 5.3 |
| %%cve:2025-55338%% | No | No | – | – | Important | 6.1 | 5.3 |
| %%cve:2025-55330%% | No | No | – | – | Important | 6.1 | 5.3 |
| %%cve:2025-55332%% | No | No | – | – | Important | 6.1 | 5.3 |
| %%cve:2025-55337%% | No | No | – | – | Important | 6.1 | 5.3 |
| %%cve:2025-55682%% | No | No | – | – | Important | 6.1 | 5.3 |
| Windows Bluetooth Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-58728%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59290%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59289%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows COM+ Event System Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-58725%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55680%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability | |||||||
| %%cve:2025-55336%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Connected Devices Platform Service (Cdpsvc) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-55326%% | No | No | – | – | Important | 7.5 | 6.5 |
| Windows Connected Devices Platform Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-58719%% | No | No | – | – | Important | 4.7 | 4.1 |
| %%cve:2025-58727%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-59191%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Cryptographic Services Information Disclosure Vulnerability | |||||||
| %%cve:2025-58720%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows DWM Core Library Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59255%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Device Association Broker Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-50174%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55677%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Digital Media Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-53150%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-50175%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows ETL Channel Information Disclosure Vulnerability | |||||||
| %%cve:2025-59197%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Error Reporting Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55692%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-55694%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Graphics Component Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59205%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-59261%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Health and Optimized Experiences Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59241%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Hello Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-53139%% | No | No | – | – | Important | 7.7 | 6.7 |
| Windows Hyper-V Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55328%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows Kernel Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59207%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-50152%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-55693%% | No | No | – | – | Important | 7.4 | 6.4 |
| %%cve:2025-59187%% | No | No | – | – | Important | 7.8 | 6.8 |
| %%cve:2025-59194%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Kernel Information Disclosure Vulnerability | |||||||
| %%cve:2025-59186%% | No | No | – | – | Important | 5.5 | 4.8 |
| %%cve:2025-55679%% | No | No | – | – | Important | 5.1 | 4.5 |
| %%cve:2025-55683%% | No | No | – | – | Important | 5.5 | 4.8 |
| %%cve:2025-55699%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Kernel Security Feature Bypass Vulnerability | |||||||
| %%cve:2025-55334%% | No | No | – | – | Important | 6.2 | 5.4 |
| Windows Local Session Manager (LSM) Denial of Service Vulnerability | |||||||
| %%cve:2025-59257%% | No | No | – | – | Important | 6.5 | 5.7 |
| %%cve:2025-59259%% | No | No | – | – | Important | 6.5 | 5.7 |
| %%cve:2025-58729%% | No | No | – | – | Important | 6.5 | 5.7 |
| Windows Management Services Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59193%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Management Services Information Disclosure Vulnerability | |||||||
| %%cve:2025-59204%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows MapUrlToZone Information Disclosure Vulnerability | |||||||
| %%cve:2025-59208%% | No | No | – | – | Important | 7.1 | 6.2 |
| Windows NTFS Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55335%% | No | No | – | – | Important | 7.4 | 6.4 |
| Windows NTLM Spoofing Vulnerability | |||||||
| %%cve:2025-59284%% | No | No | – | – | Important | 3.3 | 2.9 |
| Windows Network Driver Interface Specification Driver Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55339%% | No | No | – | – | Important | 7.8 | 6.8 |
| Windows PrintWorkflowUserSvc Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55685%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55686%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55689%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55331%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55684%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55688%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55690%% | No | No | – | – | Important | 7.0 | 6.1 |
| %%cve:2025-55691%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Push Notification Information Disclosure Vulnerability | |||||||
| %%cve:2025-59211%% | No | No | – | – | Important | 5.5 | 4.8 |
| %%cve:2025-59209%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59230%% | No | Yes | – | – | Important | 7.8 | 7.2 |
| Windows Remote Desktop Protocol Security Feature Bypass | |||||||
| %%cve:2025-55340%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Remote Desktop Services Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59202%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Resilient File System (ReFS) Deduplication Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59206%% | No | No | – | – | Important | 7.4 | 6.4 |
| %%cve:2025-59210%% | No | No | – | – | Important | 7.4 | 6.4 |
| Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-55687%% | No | No | – | – | Important | 7.4 | 6.4 |
| Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | |||||||
| %%cve:2025-55700%% | No | No | – | – | Important | 6.5 | 5.7 |
| %%cve:2025-58717%% | No | No | – | – | Important | 6.5 | 5.7 |
| Windows SMB Client Tampering Vulnerability | |||||||
| %%cve:2025-59280%% | No | No | – | – | Important | 3.1 | 2.7 |
| Windows SMB Server Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-58726%% | No | No | – | – | Important | 7.5 | 6.5 |
| Windows Search Service Denial of Service Vulnerability | |||||||
| %%cve:2025-59190%% | No | No | – | – | Important | 5.5 | 4.8 |
| %%cve:2025-59198%% | No | No | – | – | Important | 5.0 | 4.4 |
| %%cve:2025-59253%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Server Update Service (WSUS) Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59287%% | No | No | – | – | Critical | 9.8 | 8.5 |
| Windows Simple Search and Discovery Protocol (SSDP) Service Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59196%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows Speech Runtime Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-58715%% | No | No | – | – | Important | 8.8 | 7.7 |
| %%cve:2025-58716%% | No | No | – | – | Important | 8.8 | 7.7 |
| Windows State Repository API Server File Information Disclosure Vulnerability | |||||||
| %%cve:2025-59203%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Storage Management Provider Information Disclosure Vulnerability | |||||||
| %%cve:2025-55325%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Taskbar Live Preview Information Disclosure Vulnerability | |||||||
| %%cve:2025-59294%% | No | No | – | – | Important | 2.1 | 1.9 |
| Windows URL Parsing Remote Code Execution Vulnerability | |||||||
| %%cve:2025-59295%% | No | No | – | – | Important | 8.8 | 7.7 |
| Windows USB Video Class System Driver Information Disclosure Vulnerability | |||||||
| %%cve:2025-55676%% | No | No | – | – | Important | 5.5 | 4.8 |
| Windows Virtualization-Based Security (VBS) Enclave Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-53717%% | No | No | – | – | Important | 7.0 | 6.1 |
| Windows WLAN AutoConfig Service Information Disclosure Vulnerability | |||||||
| %%cve:2025-55695%% | No | No | – | – | Important | 5.5 | 4.8 |
| Xbox Gaming Services Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-59281%% | No | No | – | – | Important | 7.8 | 6.8 |
| Xbox IStorageService Elevation of Privilege Vulnerability | |||||||
| %%cve:2025-53768%% | No | No | – | – | Important | 7.8 | 6.8 |
—
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.
Heads Up: Scans for ESAFENET CDG V5 , (Mon, Oct 13th)
In January, a possible XSS vulnerability was found in the electronic document security management system ESAFENET CDG. This was the latest (as far as I can tell) in a long list of vulnerabilities in the product. Prior vulnerabilities included SQL injection issues and weaknesses in the encryption used to safeguard documents. In other words: A typical "secure" document management system. The product appears to be targeting the Chinese market, and with a website all in Chinese, I doubt it is used much, if at all, outside China.
Wireshark 4.4.10 and 4.6.0 Released, (Sun, Oct 12th)
Polymorphic Python Malware, (Wed, Oct 8th)
Today, I spoted on VirusTotal an interesting Python RAT. They are tons of them but this one attracted my attention based on some function names present in the code: self_modifying_wrapper(), decrypt_and_execute() and polymorph_code(). A polymorphic malware is a type of malware that has been developed to repeatedly mutate its appearance or signature files at every execution time. The file got a very low score of 2/64 on VT! (SHA256:7173e20e7ec217f6a1591f1fc9be6d0a4496d78615cc5ccdf7b9a3a37e3ecc3c).